EAMS(Equipment Account Management System) is a web-based terminal tool to remote access to hosts.
It supports accessing to all of SSH or RDP hosts in your VPC through the web browser.
This is a quick start guide. We will guide you from installing EAMS to connecting to your instances.
To do that, you need to have hosts to connect to.
prerequisites :
1) Network connection between EAMS and the SSH/RDP hosts.
2) Using the password authentication method for connecting to the hosts.
There is a license limit in the free version. EAMS does not have its own backup function. If you want a backup, use AWS services.
Install EAMS
When you create an instance for EAMS, the EAMS service is set to start automatically.
Just you launch the EAMS product, you can access the application via web browser at https://<public_dns>:8443
However EAMS instance need to be granted privileges to discovery your instances.
To grant privileges to EAMS instance, follow the instructions below.
Create instance profile
-
Go to https://console.aws.amazon.com/iam/home#/policies$new?step=edit
-
Switch to the JSON tab and paste the following policy. This policy grants the instance access to CloudWatch Logs to push the connection history and the ability to assume an IAM role in any account where you are running instances.
AWS Policy (eamsaws) :
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"ec2:DeleteTags",
"ec2:CreateTags"
],
"Resource": "arn:aws:ec2:*:*:instance/*"
},
{
"Sid": "VisualEditor1",
"Effect": "Allow",
"Action": [
"ssm:SendCommand",
"ssm:DescribeInstanceInformation",
"logs:CreateLogGroup",
"ssm:GetCommandInvocation"
],
"Resource": "*"
}
]
}
-
Click on Review Policy, provide a name such as eamsaws and click on Create Policy
-
Choose EC2 under services that will use this role
-
Search the following and click Next
-
AmazonEC2ReadOnlyAccess
-
AWSCloudTrailFullAccess
-
CloudWatchEventsFullAccess
-
AmazonS3FullAccess
-
AmazonSNSFullAccess
-
eamsaws (which you create in the previous step)
-
-
Provide a role name such as "EAMSAWS" and click on Create Role
-
Go to EC2 Service menu
-
Select the instance which EAMS is installed and Click on Actions → Instance Settings → Attatch/Replace IAM Role
-
Choose EAMSAWS in IAM role list. and Apply
Now you are ready to use EAMS.
Starting EAMS
In this step, We will try to access the instance from the first login.
Connect EAMS
Access EAMS Web browser.

First login
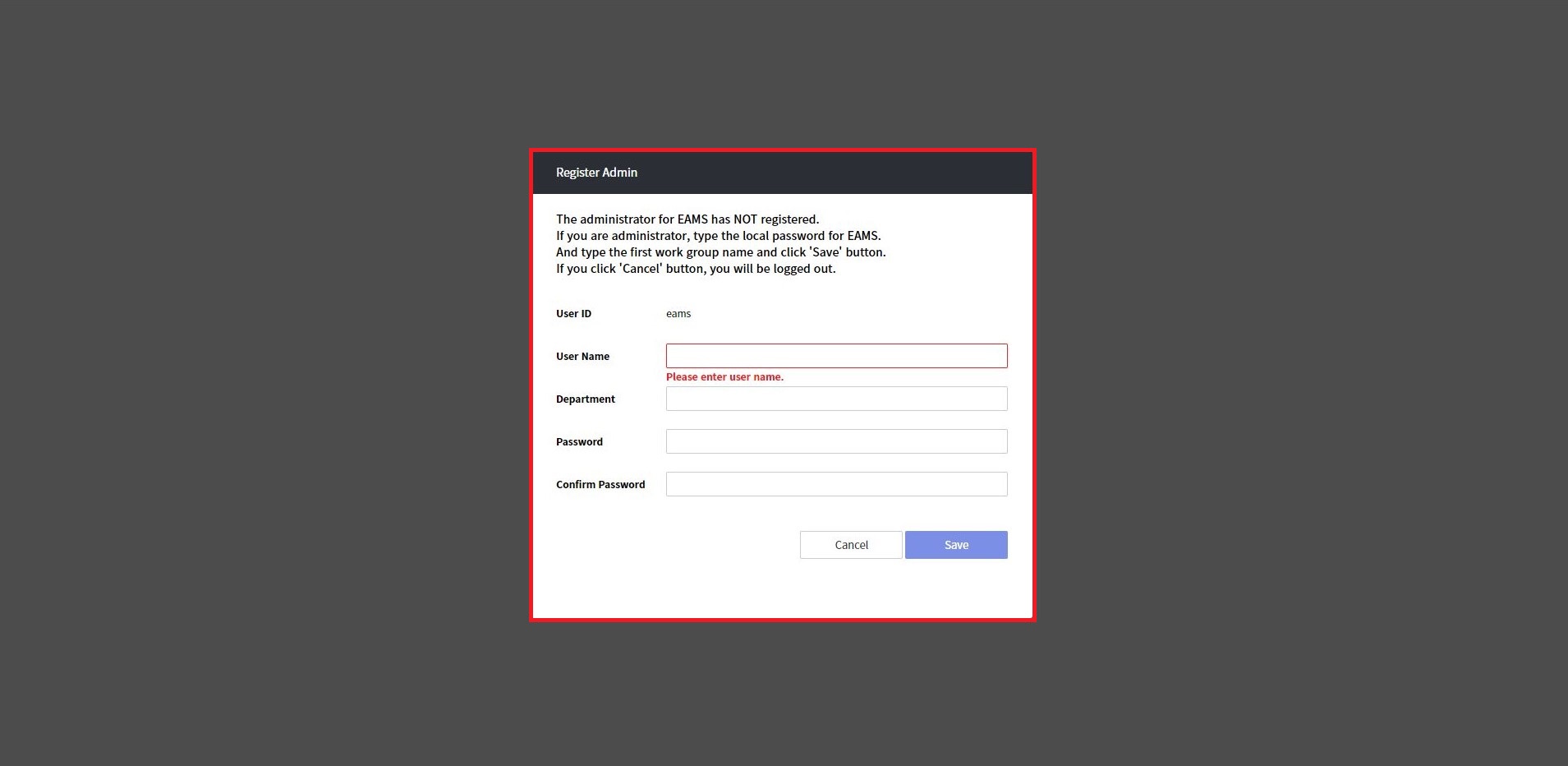
On the EAMS web, log in with ID(user defined) and instance ID as a password.

Then, you can see the popup window for Register Admin.
Enter user name, Department, Password, confirm password and save.
After register admin, return to Login page. Login again.
Connect hosts
After login, you go to the Equipment Tab screen.
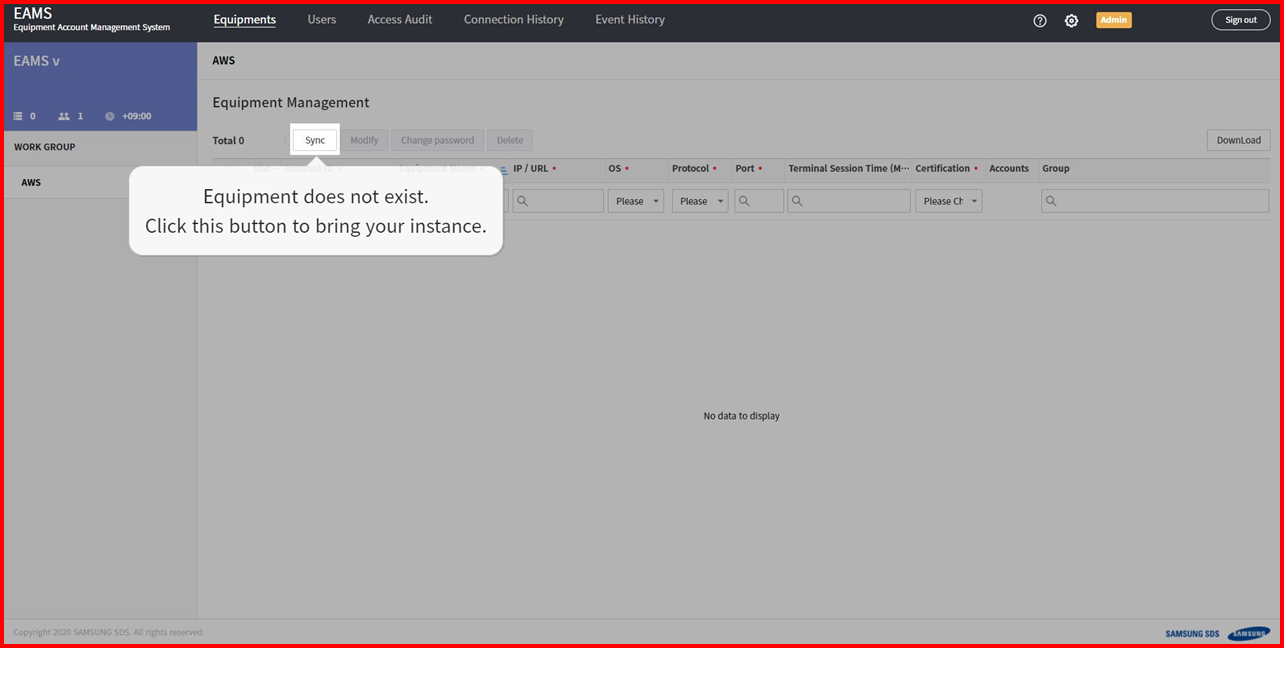
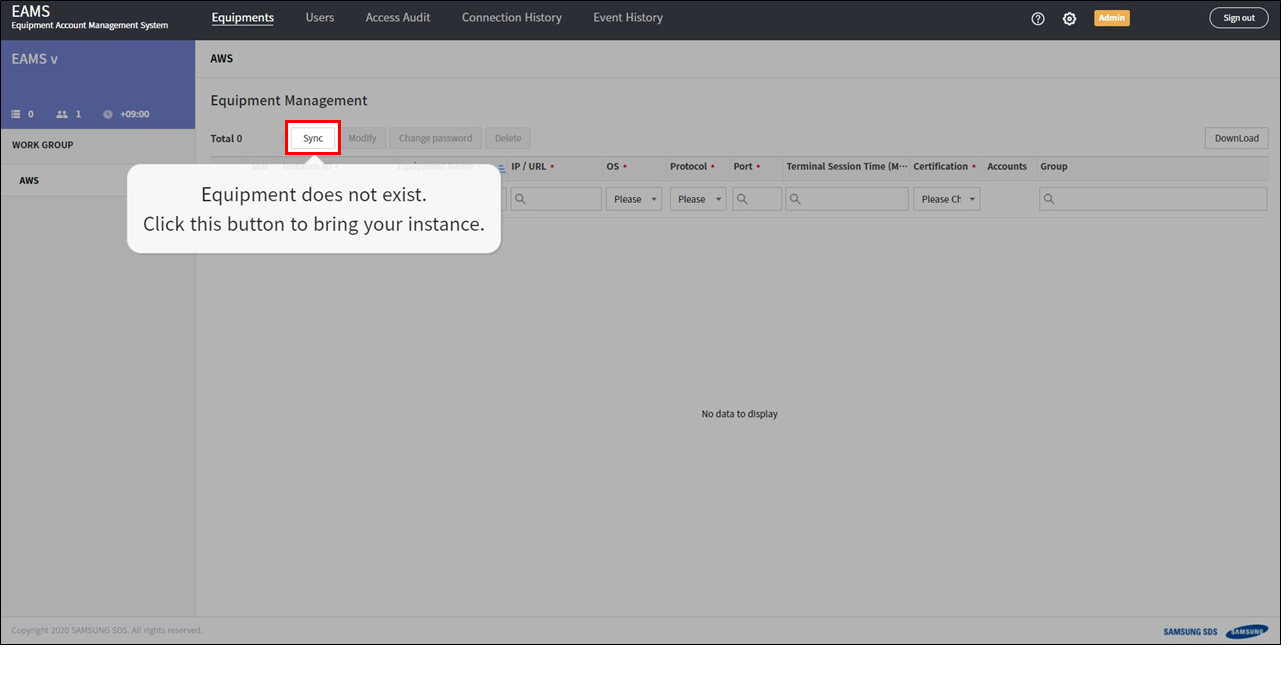
Click the sync button, EAMS will discovery your instances.
If it successful discovery, you will see a list of AWS console instances in equipment tab.
If it ends up failing, it’s probably because of privileges or network problem, so check it.
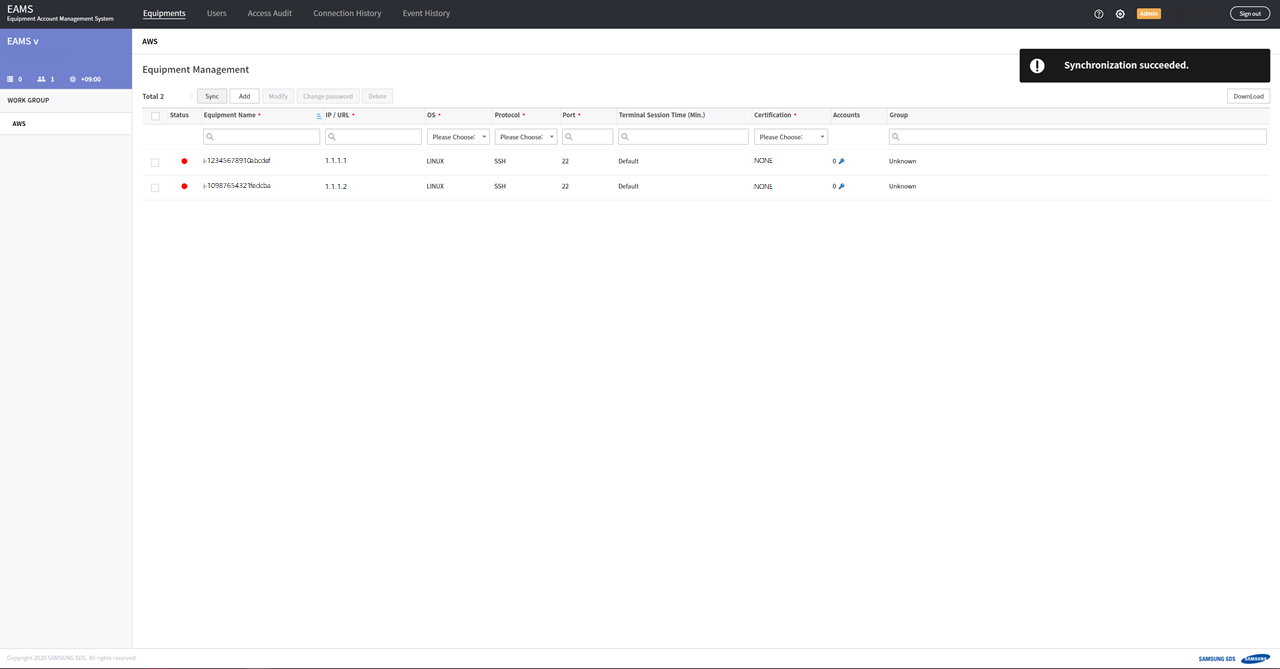
Equipments are visible on the HOME page. And each equipment has a connect buttons on the right.
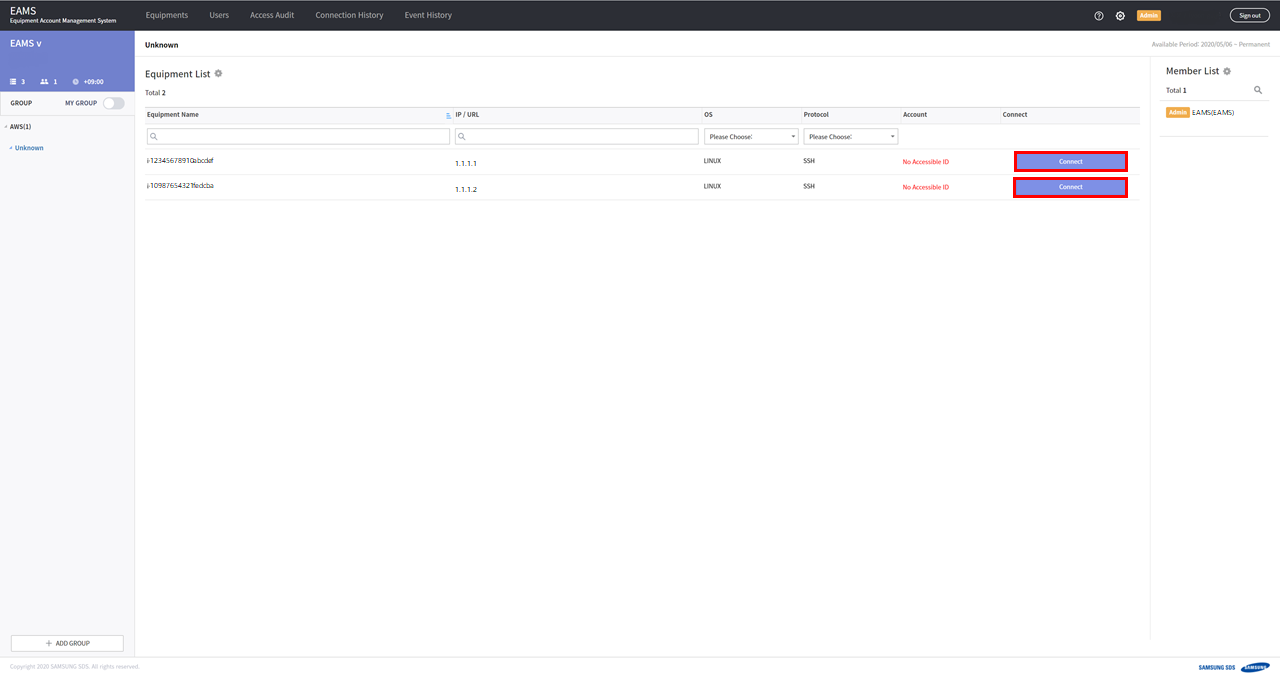
Click the connect button.
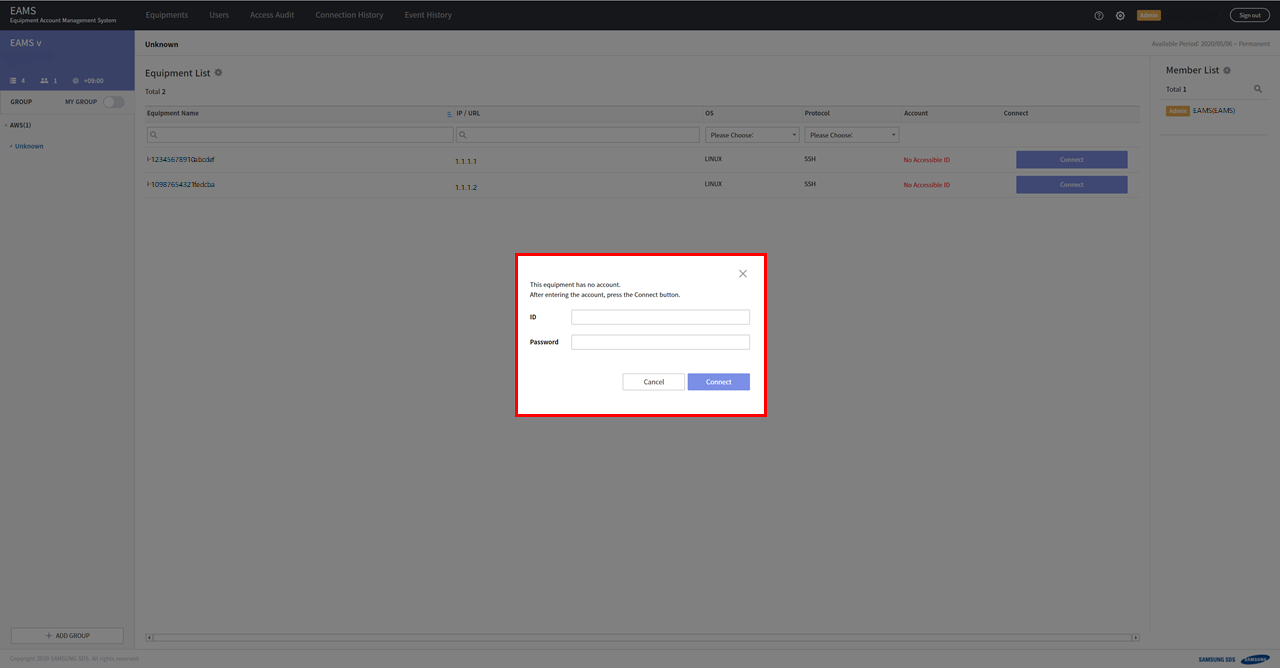
Enter the ID/Password of the instance.
If you see the terminal screen, you have successfully connected to the hosts through EAMS.

When you cannot connect to the hosts
SSH
-
Check if communication from EAMS to host
execute this command in EAMS server
telnet [host ip] 22
for example : telnet 1.1.1.1 22
When connecting normally :
$ telnet [host ip] 22 Connected to [host ip]] Escape character is '^]'
When cannot connecting :
$ telnet [host ip] 22 telnet: connect to address [host ip]: Connection timed out
If not connected, configure network inbound for AWS EC2
-
Check if Password Authentication
execute this command in EAMS server
$ cat /etc/ssh/sshd_config | grep PasswordAuthentication
If PasswordAuthentication is "no", set to "yes"
PasswordAuthentication yes
Restart ssh daemon
$ systemctl restart sshd
or
$ service sshd restart
RDP
-
Check if communication from EAMS to host
run this command in EAMS server
telnet [host ip] 3389
When connecting normally :
$ telnet [host ip] 3389 Connected to [host ip]] Escape character is '^]'
When cannot connecting :
$ telnet [host ip] 3389 telnet: connect to address [host ip]: Connection timed out
If not connected, configure network inbound for AWS EC2
-
Check if you have set an account password
-
In the Start screen, run
lusrmgr.msc -
Click
Users -
Right click on your account and click
"Set Password" -
Set password
-
Or run this command on CMD
> net user [account] [password]
for example : net user eamsadmin asdf1#
-
Check if your account is in remote desktop group
-
In the Start screen, run
lusrmgr.msc -
Click
Groups -
Add your account in
"Remote Desktop Users"
-
Or run this command on CMD
> net localgroup "Remote Desktop Users" [account] /add
for example : net localgroup "Remote Desktop Users" eamsadmin /add
-
Check if 'Authenticated Users' is in 'Access this computer from the network'
-
In the Start screen, run
secpol.msc -
Security Settings>Local Policies>User Rights Assignment -
Double click
"Access this computer from the network" -
Click
"Add User or Group" -
Enter "Authenticated Users" and click OK.
-
-
Check if not using NLA
-
In the Start screen, run
sysdm.cpl -
Click
RemoteTab -
Check "Allow connections from computers running any version of Remote Desktop"
-
Uncheck "Allow connections only from computers running Remote Desktop with Network Level Authentication"
-